News
Mind Over Matter: Cultivating Your Mental Oasis in a Fast-Paced World

Key Takeaways:
- Understanding the pillars of mental wellness
- Implementing daily practices for mental health balance
- Utilizing professional guidance to enhance well-being
- Accessing resources and communities for support
It’s easy to become engrossed in the craziness of modern life and forget about our mental health. But in the middle of life’s hectic pace, we can create a mental oasis where we may find calm and quiet. This essay will address the significance of caring for our mental health and valuable methods for setting up and maintaining a mental haven in today’s hectic world.
Table of Contents:
- The Significance of Mental Wellness
- Five Pillars of Mental Well-Being
- Daily Habits for Mental Health Maintenance
- Signs You Might Benefit from Professional Support
- How Online Platforms Can Aid in Finding Help
- Maintaining Mental Health in the Digital Age
- Community Involvement and Peer Support
- Looking Ahead: The Future of Mental Wellness Strategies
The Significance of Mental Wellness
In today’s world, where the hustle and bustle of everyday life can lead to significant stress, the role of mental health is more prominent than ever. A condition of well-being where people can manage life’s challenges, work well, and give back to their communities is known as mental health. It goes beyond simply being free from mental disease. Finding that equilibrium is essential to leading a fulfilling life, and many people are now prioritizing their mental health, recognizing when it’s time to turn to professionals, like trusted therapist in Miami, for better-coping mechanisms and strategies tailored to their lifestyle.
Five Pillars of Mental Well-Being
Mental well-being is multifaceted, incorporating various aspects of life that all contribute to overall health. The five pillars(physical, emotional, social, workplace, and societal wellness)are essential components that intertwine and impact each other. Physical wellness focuses on taking care of the body through exercise and nutrition; emotional wellness involves understanding and respecting your feelings and values; social wellness is about developing a sense of connection and belonging with others, while workplace and societal wellness involve the feelings of contribution and fulfillment in one’s occupation and a sense of responsibility towards the wider society. Balancing these pillars is critical for achieving a state of good mental health.
Daily Habits for Mental Health Maintenance
Daily habits can be essential in maintaining one’s mental health. Mindfulness helps ground individuals in the present moment, relieving the constant stream of thoughts and worries. A balanced diet provides the essential nutrients the brain needs to function correctly, while regular exercise stimulates endorphin production, leading to improved mood and energy levels. Creating time for your interests and pastimes might help you feel content and productive. These routines can increase your ability to withstand stress and maintain better mental health.
Signs You Might Benefit from Professional Support
While daily habits are a cornerstone of maintaining good mental health, there are moments when professional help is necessary. Signs that may indicate the need for support include lingering sadness or worry, significant changes in sleep patterns, eating habits, or declining enthusiasm for activities once enjoyed. Furthermore, a mental health expert may offer direction and coping mechanisms for issues related to managing relationships, overwhelming feelings all the time, or adjusting to a significant life change.
How Online Platforms Can Aid in Finding Help
The emergence of digital platforms has had a substantial influence on the way people obtain mental health services. Uch platforms break down geographical barriers, making finding a therapist that aligns with personal preferences and needs easier. It can be particularly beneficial for those who may feel uncomfortable seeking help in a traditional setting or for whom anonymity is essential.
Maintaining Mental Health in the Digital Age
While technology has facilitated access to information and support, it has also presented new challenges to mental health. Overusing digital devices and social media can lead to feelings of inadequacy and comparison, while constant connectivity can result in information overload. t is crucial to manage screen time, consciously disconnect to recharge, and engage in activities that promote mental presence and connection with the physical world.
Community Involvement and Peer Support
Community involvement and peer support play a significant role in maintaining mental wellness. Joining local groups or activities can help individuals create a sense of belonging, share experiences, and receive support from others facing similar challenges. Whether these connections are made in person or on online platforms, the sense of community they provide is vital to mental wellness and can be a source of strength and encouragement.
Looking Ahead: The Future of Mental Wellness Strategies
Our comprehension of mental health will change the methods for preserving mental well-being. A holistic approach that includes therapeutic practices, lifestyle adjustments, and supportive technologies is emerging. The future promises greater integration of evidence-based approaches with personalization to suit individual needs. Staying current on the most recent advancements in mental wellness is crucial for anybody looking to learn about successful methods of promoting mental well-being. Reputable resources such as the National Institute of Mental Health provide this information.
Conclusion
In today’s fast-paced world, prioritizing our mental health and cultivating a mental oasis where we can find peace and tranquility amidst the chaos is more important than ever. By incorporating mindfulness practices, spending time in nature, engaging in creative expression, and taking regular breaks from technology, we can create a sanctuary within ourselves where we can retreat whenever life gets overwhelming. Remember, your mental health is precious—nurture it with care and compassion, and watch as your mental oasis flourishes.
News
Unlocking the Magic of Gemstones: A Comprehensive Guide

Gemstones have captivated human fascination for centuries. From their radiant hues to their alleged metaphysical properties, these precious stones hold a unique allure. Exploring their diversity, history, and significance can be an enthralling journey. Let’s delve into a comprehensive guide to unravel the secrets of gemstones.
Introduction:
Gemstones have adorned civilizations, sparked myths, and embellished jewelry for eons. This comprehensive guide aims to demystify the world of gemstones, from their classifications to their cultural significance, helping you appreciate their beauty and value.
Types of Gemstones:
Gemstones span a vast spectrum of varieties, each boasting unique qualities. From precious diamonds to vibrant emeralds and mystical opals, explore the distinctive characteristics and allure of these different gem types.
Gemstone Meanings and Symbolism:

Beyond their aesthetic appeal, gemstones are steeped in symbolism and meaning across cultures and traditions. Uncover the significance behind specific stones and their perceived impact on emotions, healing, and spirituality.
How to Identify Authentic Gemstones:
With a plethora of synthetic and imitation gemstones flooding the market, understanding how to distinguish genuine stones is crucial. Learn the techniques and tips to authenticate and identify real gem-stones.
Popular Uses of Gemstones:
Gemstones aren’t limited to just jewelry. Discover their diverse applications in various industries, from alternative medicine to technological advancements and even artistic pursuits.
Caring for Your Gemstones:
Proper maintenance and care are essential to preserve the beauty and value of gemstones. Explore the best practices for cleaning, storing, and safeguarding your precious jewels.
Buying Guide: Choosing the Right Gemstone:
Navigating the purchase of gem-stones requires knowledge. This section provides guidance on selecting the perfect stone, considering factors like authenticity, cut, clarity, and more.
Gemstones in Culture and History:

Explore the rich tapestry of history and culture woven around gem-stones. From ancient civilizations to modern-day traditions, delve into the stories and significance of these prized jewels.
The Science Behind Gemstones:
Delve into the scientific aspects of gem-stones, understanding their formation, composition, and geological occurrences, unraveling the mysteries of their creation.
Sustainable Mining Practices in the Gemstone Industry:
Amid concerns of environmental impact, learn about sustainable mining practices and ethical considerations in the gemstone industry to support responsible sourcing.
Unlocking the Brilliance of 72 Small Gemstones
In the realm of gemstones, the allure of the small yet mighty 72 gemstones, often termed as “gemidinho de 72 pequenas lo,” holds an enigmatic charm. Exploring the exquisite world of these diminutive wonders unveils a treasure trove of beauty, history, and mystique.
Unveiling the Splendor of Gemidinho de 72 Pequenas Lo
What Makes Them Unique?
The captivating essence of the gemidinho de 72 pequenas lo lies in their exceptional rarity and distinct characteristics. These petite gemstones possess a remarkable blend of vibrant hues, captivating brilliance, and unparalleled clarity, making them a collector’s dream.
The Origin Story
Tracing Their Origins
The origin story of these 72 gemstones weaves through the annals of ancient civilizations. From whispered tales of their discovery in mystical lands to their evolution through time, each stone carries a narrative that transcends generations.
Historical Significance

These gems hold not only aesthetic appeal but also historical significance. Legends speak of their association with revered figures, attributing them with mystical powers and divine connections, amplifying their allure beyond their physical attributes.
The Allure of Rarity
Rare Treasures
The scarcity of the gemidinho de 72 pequenas lo elevates their desirability. Their limited availability adds an air of exclusivity, attracting enthusiasts, collectors, and connoisseurs alike.
Understanding Their Value
Appreciating the Intricacies
Delving into the intricacies of these gems unveils the meticulous craftsmanship and expertise required in their formation. Understanding their value involves a nuanced grasp of their rarity, color, cut, and clarity, factors that define their allure.
Embracing the Beauty
Aesthetic Appeal
The mesmerizing beauty of these gemstones transcends mere aesthetics. Their charm lies in their ability to evoke emotions, create legacies, and serve as timeless symbols of elegance and sophistication.
Investing in Elegance
The Appeal to Collectors and Connoisseurs

For collectors and connoisseurs seeking to invest in elegance, the gemidinho de 72 pequenas lo stand as a testament to refined taste and a penchant for the extraordinary.
In conclusion, the enchanting saga of the gemidinho de 72 pequenas lo encapsulates an unparalleled blend of rarity, history, and allure. As these gem-stones continue to captivate the imagination of enthusiasts worldwide, their timeless appeal persists, making them a coveted treasure in the world of precious stones.
FAQs:
1. What are birthstones, and how are they determined?
Birthstones are gems associated with specific months and are often linked to a person’s birth month.
2. Are synthetic gem-stones less valuable than natural ones?
Synthetic gem-stones can be equally valuable based on their quality, but their value may differ from natural stones.
3. Can gem-stones affect one’s energy or well-being?
Beliefs about gem-stones affecting energy or well-being vary among individuals and cultures. Scientific evidence supporting this is limited.
4. How do I know if a gemstone is authentic?
Consulting a certified gemologist or using gemological testing tools can help authenticate gem-stones.
5. What is the rarest gemstone?
Various gem-stones are considered rare, with some like red diamonds or jadeite commanding exceptionally high prices due to scarcity.
6. Can gemstones lose their color or luster over time?
Improper care or exposure to harsh conditions can affect a gemstone’s appearance over time.
7. What is the significance of wearing certain gem-stones?
Different cultures attribute various meanings and significance to wearing specific gem-stones, often tied to beliefs in luck, protection, or healing properties.
8. How can I clean my gemstone jewelry at home?
Cleaning methods vary based on the gemstone. Generally, mild soap, water, and a soft brush can be used for gentle cleaning.
9. Are there ethical concerns in the gemstone industry?
Yes, unethical mining practices and issues related to labor rights and environmental damage exist in the gemstone industry.
10. Can gemstones be an investment?
While some gem-stones can appreciate in value, investing in them requires thorough research and understanding of the market.
Conclusion:
The allure of gemstones extends far beyond their dazzling appearance. This guide aimed to unlock the mysteries surrounding these precious jewels, exploring their cultural, historical, and scientific facets. Embrace the magic of gemstones, appreciating their beauty while understanding their profound significance across civilizations.
News
Unlocking the Power of WordfinderX: A Comprehensive Guide to Effective Keyword Research
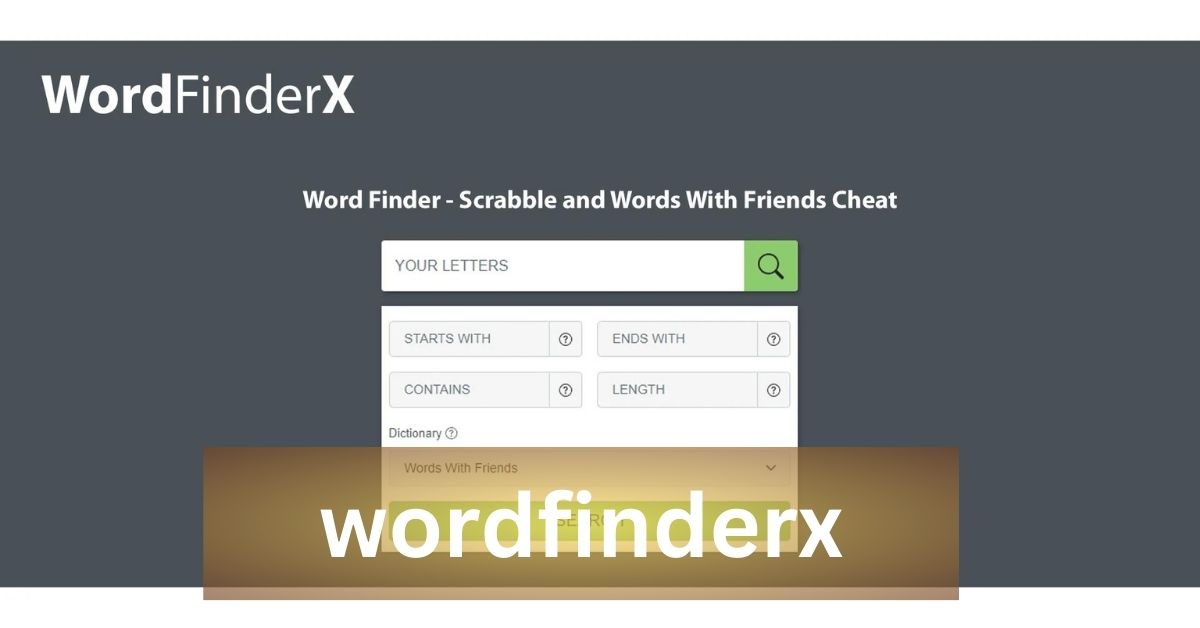
Explore the potential of WordfinderX for impeccable keyword research. Dive into this comprehensive guide to learn how to optimize your content strategy with the right keywords.
Introduction:
In the ever-evolving digital landscape, keyword research remains a cornerstone of successful content strategy. WordfinderX emerges as a powerful tool, offering insights and opportunities for website optimization. This guide unveils the intricacies of leveraging WordfinderX to its fullest potential. Dive into these sections to master the art of keyword research:
Understanding WordfinderX
WordfinderX, a robust keyword research tool, provides a comprehensive database for identifying relevant search terms. With an intuitive interface and extensive database, it simplifies the process of discovering keywords tailored to your niche.
Utilizing Advanced Features
Delve deeper into WordfinderX’s advanced
functionalities, including filtering options, competitor analysis, and trend tracking. Uncover hidden gems by harnessing these features to refine your keyword selections.
Crafting High-Impact Content
Learn how to integrate identified keywords seamlessly into your content. Craft engaging and SEO-optimized articles, blogs, or web pages to enhance visibility and attract organic traffic.
Implementing SEO Strategies
Leverage WordfinderX insights to implement proven SEO strategies. From on-page optimization to backlink building, explore tactics to boost your website’s search engine rankings.
Analyzing Keyword Trends
Stay ahead in the dynamic digital landscape by understanding keyword trends. WordfinderX equips you with the tools to analyze and adapt to changing search behaviors effectively.
Navigating Competitive Landscape
Uncover your competitors’ keyword strategies and gain insights to refine your own. WordfinderX aids in dissecting competitor keywords, allowing you to strategize for a competitive edge.
Optimizing Local SEO
Explore the nuances of local SEO through WordfinderX. Enhance your visibility in local searches by targeting location-specific keywords and optimizing your online presence.
Integrating Long-Tail Keywords
Discover the potential of long-tail keywords in attracting targeted traffic. Learn how WordfinderX facilitates the identification and integration of long-tail keywords for improved conversion rates.
Expanding Semantic Search
Explore the world of semantic search and its impact on keyword relevance. WordfinderX assists in identifying semantically related terms for a more holistic content strategy.
Measuring Success Metrics
Unravel the metrics that matter. Learn how to track and measure the success of your keyword strategies using WordfinderX’s analytical tools.
Unveiling the Power of WordfinderX
In the vast landscape of digital content creation, mastering the art of keyword research stands as a pivotal gateway to achieving optimal visibility and resonance with your audience. Enter WordfinderX, a revolutionary tool reshaping the landscape of keyword exploration and content optimization. In this comprehensive guide, we delve deep into the functionalities, strategies, and advantages of WordfinderX, empowering you to harness its potential and elevate your online presence.
Understanding WordfinderX: Redefining Keyword Exploration
WordfinderX emerges as a cutting-edge solution engineered to streamline the intricate process of keyword research. Its intuitive interface and robust algorithms enable users to unearth a treasure trove of keywords relevant to their niche, fostering precision and efficiency in content optimization.
Unraveling the Features: Empowering Content Strategy
Seamless Keyword Discovery
With WordfinderX, embark on a journey of seamless keyword discovery. Its extensive database presents a myriad of relevant keywords, unveiling hidden gems that align precisely with your content objectives. From long-tail phrases to trending terms, this tool is a goldmine for comprehensive keyword lists.
In-depth Analytics
Beyond mere keyword suggestions, WordfinderX offers in-depth analytics, providing valuable insights into search volume, competitiveness, and trends. This analytical prowess empowers content creators with data-driven decision-making capabilities, ensuring strategic alignment with audience preferences.
Competitive Edge
Gain a competitive edge by leveraging WordfinderX’s competitive analysis feature. Uncover the strategies employed by industry competitors, identify gaps, and capitalize on untapped keyword opportunities, positioning your content ahead in the digital race.
Strategies for Optimal Utilization: Maximizing Keyword Potential
Long-Term Keyword Planning
Craft a robust content strategy by harnessing WordfinderX for long-term keyword planning. Identify evergreen keywords and trends, enabling sustained organic traffic growth and enhanced visibility across diverse search engines.
Content Optimization
Elevate the quality and relevance of your content through meticulous optimization using WordfinderX-generated keywords. Seamlessly integrate these terms into your titles, meta descriptions, and body content, enriching your material for both search engines and users.
Niche Targeting
WordfinderX empowers precise niche targeting by uncovering specialized keywords. Tailor your content to resonate deeply within specific audience segments, fostering engagement and establishing authority within your domain.
Leveraging WordfinderX for Success: Unlocking Your Digital Potential
WordfinderX transcends the conventional realms of keyword research, transcending into a realm of digital empowerment. Embrace this tool as your ally in navigating the intricate maze of online visibility, propelling your content to the forefront of search engine rankings.
FAQs about WordfinderX:
- Is WordfinderX suitable for beginners? WordfinderX caters to users of all levels. Its user-friendly interface makes it accessible for beginners while offering advanced features for seasoned marketers.
- Can WordfinderX be used for multiple websites? Yes, WordfinderX allows users to research keywords for multiple websites, offering flexibility for various projects.
- Does WordfinderX provide real-time keyword data? Absolutely, WordfinderX offers real-time keyword data, ensuring you access the most updated information for your strategies.
- Is WordfinderX compatible with other SEO tools? Yes, WordfinderX integrates seamlessly with various SEO tools, facilitating a comprehensive approach to optimization.
- Can WordfinderX track keyword performance over time? Indeed, WordfinderX includes tracking features to monitor keyword performance and adapt strategies accordingly.
- Does WordfinderX offer customer support? Yes, WordfinderX provides comprehensive customer support to assist users with any queries or issues they might encounter.
- Is there a free trial available for WordfinderX? Yes, there’s a free trial period offered by WordfinderX for users to explore its features and functionalities.
- Can WordfinderX suggest keyword variations? Absolutely, WordfinderX excels in suggesting relevant keyword variations based on search queries.
- Does WordfinderX offer competitor analysis? Yes, WordfinderX provides in-depth competitor analysis tools to understand competitor strategies.
- Can WordfinderX help in optimizing content for voice search? Certainly, WordfinderX aids in identifying keywords tailored for voice search optimization.
Conclusion:
WordfinderX emerges as an indispensable tool in the arsenal of marketers, SEO specialists, and content creators. By unlocking its potential, you pave the way for an optimized content strategy that resonates with your audience and elevates your online presence. Master the art of keyword research with WordfinderX, and watch your digital endeavors flourish.
News
Innovative Approaches to Designing Food Display Solutions for Retail Environments

Table of Contents
- Introduction to Food Display Solutions
- Importance of Effective Food Displays
- Types of Food Displays
- Design Principles for Food Displays
- The Role of Technology in Modern Food Displays
- Case Studies: Success Stories
- Sustainability in Food Display Solutions
- Future Trends in Food Display Design
Introduction to Food Display Solutions
Food display solutions have transformed from mere storage options to essential components of a thriving retail environment. These display units are designed to do more than hold food items—they are crafted to create an appealing visual experience that can draw customers’ eyes and entice them to purchase. Investing in high-quality hot food display equipment ensures that food remains at the optimal temperature and is showcased in a way that highlights its best qualities, enhancing the product’s perceived value.
The way products are displayed plays a critical role in shaping customer experience within a store. Stores that capitalize on visually appealing and strategically placed displays can create a more engaging shopping atmosphere that encourages sales and builds brand loyalty. As competition in the retail sector intensifies, businesses must prioritize innovative display solutions beyond mere functionality and deliver a visually compelling experience for their customers.
Importance of Effective Food Displays
Adequate food displays in retail settings must be considered. These displays influence how consumers perceive products and make purchasing decisions. A well-executed display attracts attention, enhances the shopping experience, and drives sales. According to a comprehensive analysis of retail strategies, product presentation is a key determinant of consumer engagement and satisfaction.
Furthermore, effective displays reduce food waste by encouraging timely purchases, thus ensuring fresh stock turnover. By enticing customers with visually appealing and easily accessible displays, retailers can facilitate faster product movement, reducing the likelihood of spoilage and maximizing profitability.
Types of Food Displays
Food displays come in various formats, each suited to different products and retail settings. Refrigerated displays, for instance, are crucial for preserving the freshness and safety of perishable items such as dairy, meats, and certain beverages. These units maintain low temperatures to prevent spoilage and ensure product safety.
Conversely, heated displays are ideal for ready-to-eat meals, keeping food warm and inviting until purchase. Ambient displays cater to items that do not require specific temperature controls, like baked goods and dry snacks. These different display types are often customized with features such as adjustable shelving, specialized lighting, and transparent materials to showcase the food effectively and enhance its appeal and accessibility.
Design Principles for Food Displays
Designing an effective food display involves more than arranging products on a shelf. Key design principles that play a significant role include accessibility, visibility, and hygiene. Accessibility ensures that customers can easily reach all products, encouraging interaction and purchase.
Visibility is also paramount; products should be organized and illuminated to highlight their features, making them irresistible to shoppers. Hygiene cannot be compromised, with every display aspect designed to maintain cleanliness and prevent contamination. Explore this informative guide on retail design for more insights into how these principles are applied.
The Role of Technology in Modern Food Displays
Technology catalyzes innovation in food displays, making them more interactive and efficient. Digital signage, for instance, allows retailers to update promotional content in real time, highlight special offers, or present nutritional information to educate customers while they shop.
Innovative shelf technologies equipped with sensors can notify staff when stock is low or a unit requires maintenance, thus ensuring seamless operation and minimal disruption. Advanced refrigeration technologies also contribute to sustainability by optimizing energy use without compromising the freshness and quality of the displayed products.
Case Studies: Success Stories
Retailers globally are reaping the benefits of investing in innovative food display solutions. A case in point is a well-known supermarket chain that redesigned its store layout, focusing heavily on the visual appeal of its food displays. This strategic move resulted in increased foot traffic and a notable rise in sales volumes, demonstrating the power of well-thought-out display solutions in attracting and retaining customers.
Sustainability in Food Display Solutions
With growing environmental consciousness, sustainability in food display solutions is no longer optional but necessary. Retailers increasingly adopt energy-efficient technologies and sustainable materials like recycled glass and low-impact composites to construct display units.
These initiatives help reduce an organization’s environmental footprint while simultaneously cutting utility costs over time. Implementing LED lighting and opting for units with energy-efficient systems underscores a commitment to sustainability and often enhances a company’s brand image as an environmentally responsible operator.
Future Trends in Food Display Design
Technological developments and shifting consumer preferences are expected to significantly impact food display design. Personalizing the shopping experience through integrating data analytics, which can provide customized product recommendations based on individual consumer behavior, is becoming increasingly popular. Future displays will probably emphasize accurate product sources and thorough nutritional information in response to the growing consumer desire for openness. This openness promotes a satisfying buying experience by increasing consumer trust and assisting them in making wise decisions. Leaders in the ever-changing market will probably be retailers who adopt these trends.
-

 News1 year ago
News1 year agoVaping: Beyond the Hype – Unveiling the Risks and Realities
-

 Entertainment2 years ago
Entertainment2 years agoUnleashing Geekdom: Exploring the Wonders of Geekzilla Radio
-

 Fashion1 year ago
Fashion1 year agoWhat is λιβαισ? A Complete Guide
-

 News2 years ago
News2 years agoThe Travel Resorts of America lawsuit (Legal Controversy)
-

 Games2 years ago
Games2 years agoHow To Play Baduk game: Unveiling the Art of Strategic Brilliance
-

 News2 years ago
News2 years agoAbraham Quiros Villalba: Unveiling the Journey of a Visionary
-

 Life style1 year ago
Life style1 year agoDemystifying λυσασ: Unveiling the Enigmatic Concept
-

 Tech1 year ago
Tech1 year agoUnlocking the Secrets of 02045996875: UK’s Unique
