Tech
chargomez1: Revolutionizing the Digital Landscape

A. Definition of chargomez1
chargomez1, a cutting-edge technological marvel, is redefining the way we engage with digital platforms. It encompasses a range of features designed to streamline processes and enhance user experiences.
B. Importance in the Digital World
As our dependency on digital solutions grows, the significance of chargomez1 becomes increasingly apparent. Its versatile applications span across sectors, making it a crucial tool in the modern era.
II. c
A. Historical Background
To understand the prowess of chargomez1, it’s essential to delve into its historical roots. From its inception to present-day advancements, we’ll trace the journey that led to its current state.
B. Technological Advancements
The evolution of chargomez1 aligns with rapid technological progress. We’ll explore how advancements in AI and data processing have contributed to the sophistication of chargomez1.
III. Understanding the Functionality
A. Key Features
Navigating through the intricate details, we’ll uncover the key features that set chargomez1 apart. From seamless integration to user-friendly interfaces, each element plays a pivotal role.
B. How chargomez1 Works
Demystifying the technological magic, we’ll provide insights into the inner workings of chargomez1. A simplified breakdown will enhance comprehension for both tech enthusiasts and novices.
IV. Applications of chargomez1
A. In the Business Sector
The business realm has embraced chargomez1 for its transformative impact. We’ll explore case studies and success stories of businesses leveraging chargomez1 for enhanced efficiency and productivity.
B. Personal Use and Benefits
Beyond corporate applications, chargomez1 offers benefits to individual users. From managing personal tasks to optimizing daily routines, we’ll uncover the personal advantages it brings.
V. Advantages and Disadvantages
A. Pros of Using chargomez1
The advantages of incorporating chargomez1 into workflows are plentiful. Increased speed, accuracy, and adaptability are among the many benefits that users can harness.
B. Potential Drawbacks
However, no technology is without its challenges. We’ll address potential drawbacks, ensuring a balanced perspective on the limitations of chargomez1.
VI. Future Trends
A. Emerging Technologies in chargomez1
As technology advances, so does chargomez1. We’ll explore the latest trends and upcoming features that promise to elevate the capabilities of this innovative solution.
B. Predictions and Possibilities
Envisioning the future, we’ll discuss potential directions for chargomez1, considering its role in shaping the technological landscape.
VII. How to Choose the Right chargomez1
A. Factors to Consider
Selecting the right chargomez1 solution requires careful consideration. We’ll provide a comprehensive guide, highlighting key factors to help users make informed decisions.
B. Tips for Decision-Making
Navigating the market can be overwhelming. Practical tips for decision-making will empower readers to choose a chargomez1 solution tailored to their needs.
VIII. Success Stories
A. Real-World Examples
Success stories from various industries will exemplify how chargomez1 has contributed to achieving goals, overcoming challenges, and driving positive outcomes.
B. Testimonials and User Experiences
The firsthand experiences of users will provide valuable insights, offering a glimpse into the real-world impact of chargomez1.
IX. Tips for Optimal Usage
A. Maximizing Benefits
To fully harness the potential of chargomez1, users need to optimize its usage. Practical tips and strategies will guide users towards maximizing benefits.
B. Overcoming Common Challenges
Challenges may arise in the integration and utilization of chargomez1. We’ll provide actionable solutions to common issues, ensuring a smooth user experience.
X. chargomez1 vs. Competitors
A. A Comparative Analysis
Pitting chargomez1 against its competitors, we’ll conduct a thorough analysis. Understanding the unique selling points will assist users in making informed choices.
B. Unique Selling Points
Highlighting the distinctive features that set chargomez1 apart, we’ll showcase why it stands out in a crowded market.
XI. Industry Impact
A. Influence on Various Sectors
From healthcare to finance, we’ll explore how chargomez1 is influencing diverse industries. Case studies will illustrate its widespread impact.
B. Future Implications
Examining the broader implications, we’ll discuss how the widespread adoption of chargomez1 could shape the future of industries worldwide.
XII. Security and Privacy Concerns
A. Ensuring Data Safety
In an era of heightened concerns about data security, we’ll delve into the measures in place to ensure the safety of user data within the chargomez1 ecosystem.
B. Addressing User Concerns
Addressing common apprehensions, we’ll provide transparency on how chargomez1 addresses user concerns related to privacy and security.
Features and Capabilities
Advanced Technological Components Chargomez1 boasts cutting-edge technological components that set it apart in the digital landscape. From AI-driven algorithms to seamless integration with various digital platforms, it’s designed to meet the demands of modern businesses.
Integration with Digital Platforms One of Chargomez1’s strengths lies in its ability to seamlessly integrate with a myriad of digital platforms. This ensures a smooth workflow for businesses, allowing them to harness the full potential of Chargomez1.
User-Friendly Interface Despite its advanced features, Chargomez1 maintains a user-friendly interface. Its intuitive design makes it accessible to both tech-savvy professionals and those new to digital technologies.
Impact on Digital Businesses
Enhanced Digital Marketing Strategies Chargomez1 has proven to be a game-changer in digital marketing. Its analytics and optimization tools empower businesses to refine their strategies, ensuring maximum reach and impact.
Increased Efficiency in Online Operations Digital businesses leveraging Chargomez1 report heightened efficiency in their online operations. Automation features and streamlined processes contribute to improved productivity and reduced operational bottlenecks.
Case Studies
Success Stories of Companies using Chargomez1 Numerous companies have experienced unprecedented success by incorporating Chargomez1 into their operations. These success stories serve as testimonials to the efficacy of Chargomez1 in achieving digital goals.
Real-world Applications and Benefits From e-commerce giants to small startups, Chargomez1’s real-world applications and benefits span across industries. It has proven adaptable to diverse business models, showcasing its versatility.
Future Trends and Developments
Predictions for Chargomez1 in the Coming Years Experts predict a promising future for Chargomez1, with continual advancements and features on the horizon. Businesses are advised to stay abreast of these developments to remain competitive in the ever-evolving digital landscape.
Potential Improvements and Upgrades Chargomez1’s commitment to innovation suggests ongoing improvements and upgrades. Users can anticipate enhanced functionalities and features that cater to emerging digital trends.
User Testimonials
Positive Experiences with Chargomez1 Users worldwide express their satisfaction with Chargomez1, highlighting its impact on their digital endeavors. Positive experiences underscore the reliability and effectiveness of this digital solution.
Feedback from Digital Professionals Digital professionals, from marketers to developers, share their feedback on how Chargomez1 has positively influenced their work. Their insights provide valuable perspectives for those considering the adoption of Chargomez1.
Challenges and Solutions
Common Issues Faced by Users No digital solution is without challenges. Chargomez1 users may encounter common issues, but understanding these challenges is the first step toward effective resolution.
How Chargomez1 Addresses and Resolves Challenges Chargomez1 is not only about features but also about robust solutions. Explore how Chargomez1 addresses and resolves challenges, ensuring a smooth experience for users.
Comparison with Competitors
Strengths and Weaknesses in Comparison In a competitive digital landscape, it’s essential to assess how Chargomez1 stacks up against its competitors. Understanding its strengths and weaknesses aids businesses in making informed decisions.
Unique Selling Points of Chargomez1 Chargomez1’s unique selling points set it apart in the market. Whether it’s unparalleled features, exceptional customer support, or a strong user community, these aspects contribute to its appeal.
Tips for Optimizing Chargomez1
Best Practices for Maximum Efficiency Optimizing Chargomez1 requires a strategic approach. Learn the best practices that ensure maximum efficiency, allowing businesses to extract the full potential of this revolutionary tool.
Customization Options and Settings Chargomez1 offers customization options and settings to tailor its functionalities to the specific needs of users. Understanding these options is key to optimizing its performance.
Chargomez1 Community
Online Forums and Communities Joining the Chargomez1 community opens doors to collaboration and networking. Explore online forums and communities where users share insights, tips, and experiences related to Chargomez1.
Collaboration and Networking Opportunities The Chargomez1 community provides opportunities for collaboration and networking. Engage with like-minded professionals, fostering connections that can contribute to your digital success.
Pricing Plans
Overview of Chargomez1 Pricing Structure Before diving into Chargomez1, understanding its pricing structure is crucial. This section provides an overview, ensuring businesses make informed decisions based on their budget and needs.
Value for Money and Cost Efficiency Assessing the value for money and cost efficiency of Chargomez1 is essential. This section explores how businesses can maximize their ROI through the adoption of Chargomez1.
Security Measures
Data Protection and Privacy Features In an era of increasing digital threats, Chargomez1 prioritizes data protection and privacy. Explore the security measures in place to safeguard user information.
Trustworthiness of Chargomez1 Trust is paramount in the digital landscape. Understand why Chargomez1 is regarded as a trustworthy solution, providing users with confidence in their digital operations.
Regulatory Compliance
Adherence to Digital Regulations Chargomez1 adheres to digital regulations to ensure legal compliance. Explore the measures in place, guaranteeing that businesses using Chargomez1 operate within the boundaries of applicable laws.
Legal Implications and Compliance Understanding the legal implications and compliance aspects associated with Chargomez1 is crucial for businesses aiming for ethical and legal digital practices.
Conclusion
In conclusion, Chargomez1 has emerged as a transformative force, revolutionizing the digital landscape. Its impact on digital businesses, coupled with ongoing developments and a supportive community, positions Chargomez1 as a leading solution for those navigating the complexities of the digital era.
FAQs
- Is Chargomez1 suitable for small businesses?
- Yes, Chargomez1 offers scalability, making it suitable for businesses of all sizes.
- What sets Chargomez1 apart from other digital solutions?
- Chargomez1 distinguishes itself through advanced features and a user-friendly interface.
- How can I join the Chargomez1 community?
- Visit the official website to access forums and community features.
- Are there any upcoming updates for Chargomez1?
- Stay tuned to official announcements for information on upcoming updates.
- What security measures does Chargomez1 have in place?
- Chargomez1 prioritizes data protection, implementing robust security measures.
Tech
thesparkshop.in:product/wireless-earbuds-bluetooth-5-0-8d-stereo-sound-hi-fi

In today’s fast-paced world, music is not just a pastime; it’s a companion that accompanies us through every facet of life. Whether we’re commuting, working out, or simply relaxing at home, having the perfect pair of earbuds can make all the difference. Enter thesparkshop.in:product/wireless-earbuds-bluetooth-5-0-8d-stereo-sound-hi-fi from thesparkshop.in, promising an unparalleled auditory experience coupled with the convenience of wireless technology.
Cutting-Edge Technology:
At the heart of these wireless earbuds lies the advanced Bluetooth 5.0 technology. This latest iteration of Bluetooth offers significant advantages over its predecessors, including faster transmission speeds, increased range, and improved connectivity. With Bluetooth 5.0, you can enjoy seamless pairing with your devices, whether it’s your smartphone, tablet, or laptop, ensuring hassle-free audio streaming without any interruptions.
Immersive Audio Experience:
One of the standout features of these earbuds is their 8D stereo sound capability. Unlike conventional stereo sound, which only offers two audio channels (left and right), 8D sound takes immersion to a whole new level by adding depth and dimension to the listening experience. With these wireless earbuds, you’ll feel like you’re right in the middle of the music, with every note, beat, and melody coming to life in stunning clarity and detail.
Comfort and Convenience:
Designed with user comfort in mind, these wireless earbuds feature a lightweight and ergonomic design that fits snugly in your ears without causing any discomfort, even during extended listening sessions. The included charging case not only keeps your earbuds safe and secure but also doubles as a portable power bank, ensuring that you never run out of battery when you’re on the go.
Seamless Connectivity:
Thanks to the built-in touch controls, managing your music playback, answering calls, and accessing your device’s voice assistant is as easy as a tap or swipe. Whether you’re adjusting the volume, skipping tracks, or activating Siri or Google Assistant, you can do it all with just a few simple gestures, eliminating the need to fumble with your device while you’re on the move.
Long-Lasting Battery Life:
With up to X hours of playtime on a single charge, these wireless earbuds are perfect for all-day use, whether you’re at work, at the gym, or on a long journey. And when it’s time to recharge, simply pop them back into the charging case for a quick top-up, ensuring that your music never skips a beat.
Conclusion:
In conclusion, the Wireless Earbuds with Bluetooth 5.0 and 8D Stereo Sound from thesparkshop.in offer a winning combination of cutting-edge technology, immersive audio experience, comfort, and convenience. Whether you’re a music enthusiast, a fitness fanatic, or a busy professional, these earbuds are sure to enhance every aspect of your audio journey. Say goodbye to tangled wires and mediocre sound quality, and say hello to true wireless freedom with these state-of-the-art earbuds.
In today’s fast-paced world, music is not just a pastime; it’s a companion that accompanies us through every facet of life. Whether we’re commuting, working out, or simply relaxing at home, having the perfect pair of earbuds can make all the difference. Enter the Wireless Earbuds with Bluetooth 5.0 and 8D Stereo Sound from thesparkshop.in, promising an unparalleled auditory experience coupled with the convenience of wireless technology.
Cutting-Edge Technology:
At the heart of these wireless earbuds lies the advanced Bluetooth 5.0 technology. This latest iteration of Bluetooth offers significant advantages over its predecessors, including faster transmission speeds, increased range, and improved connectivity. With Bluetooth 5.0, you can enjoy seamless pairing with your devices, whether it’s your smartphone, tablet, or laptop, ensuring hassle-free audio streaming without any interruptions.
Immersive Audio Experience:
One of the standout features of these earbuds is their 8D stereo sound capability. Unlike conventional stereo sound, which only offers two audio channels (left and right), 8D sound takes immersion to a whole new level by adding depth and dimension to the listening experience. With these wireless earbuds, you’ll feel like you’re right in the middle of the music, with every note, beat, and melody coming to life in stunning clarity and detail.
Comfort and Convenience:
Designed with user comfort in mind, these wireless earbuds feature a lightweight and ergonomic design that fits snugly in your ears without causing any discomfort, even during extended listening sessions. The included charging case not only keeps your earbuds safe and secure but also doubles as a portable power bank, ensuring that you never run out of battery when you’re on the go.
Seamless Connectivity:
Thanks to the built-in touch controls, managing your music playback, answering calls, and accessing your device’s voice assistant is as easy as a tap or swipe. Whether you’re adjusting the volume, skipping tracks, or activating Siri or Google Assistant, you can do it all with just a few simple gestures, eliminating the need to fumble with your device while you’re on the move.
Long-Lasting Battery Life:
With up to X hours of playtime on a single charge, these wireless earbuds are perfect for all-day use, whether you’re at work, at the gym, or on a long journey. And when it’s time to recharge, simply pop them back into the charging case for a quick top-up, ensuring that your music never skips a beat.
Conclusion:
In conclusion,thesparkshop.in:product/wireless-earbuds-bluetooth-5-0-8d-stereo-sound-hi-fi from thesparkshop.in offer a winning combination of cutting-edge technology, immersive audio experience, comfort, and convenience. Whether you’re a music enthusiast, a fitness fanatic, or a busy professional, these earbuds are sure to enhance every aspect of your audio journey. Say goodbye to tangled wires and mediocre sound quality, and say hello to true wireless freedom with these state-of-the-art earbuds.
Tech
MySCAD Revolutionizing Education with Innovative Technology

Introduction:
Savannah College of Art and Design (SCAD) has long served as a beacon for creatives looking to develop their skills and pursue their passions in the fields of art and design. MySCAD, our institution’s innovative online platform, serves as a digital gateway for students, faculty and staff to seamlessly navigate the rich range of opportunities SCAD offers.
User-friendly interface:
MySCAD’s user-friendly interface is designed with the student experience in mind. Easy access to courses, resources and campus updates allows students to reduce administrative hurdles and focus on their creative pursuits. The platform can be accessed through a web browser or mobile device, giving users the ability to stay connected anytime, anywhere.
Academic support and resources:
One of the distinctive features of MySCAD is its comprehensive academic support system. Students have access to a variety of resources, including class schedules, syllabi, and academic calendars. The platform facilitates communication between students and teachers through an integrated messaging system and promotes a collaborative learning environment.
In addition, MySCAD provides a centralized location for accessing educational materials, digital libraries, and multimedia resources. This ensures that students have the tools they need to succeed in the classroom and reach their full creative potential.
Campus life and events:
MySCAD goes beyond academics and serves as a virtual portal to campus life. This platform informs students about upcoming events, exhibitions and workshops, and fosters a sense of community within the SCAD family. Through gallery openings, guest lectures by renowned artists, and student initiatives, MySCAD ensures that students participate in the vibrant cultural heritage that SCAD fosters.
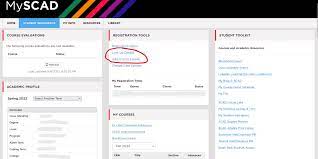
Collaboration and networking:
MySCAD is more than just a repository of information. It acts as a catalyst for collaboration and networking. The platform features discussion forums, spaces to share projects, and group collaboration tools that allow students to connect with peers, exchange ideas, and collaborate on projects. This relationship not only enhances the learning experience, but also reflects the collaborative nature of the creative industries.
Career development:
MySCAD’s core mission is to prepare students for success beyond the classroom. The platform integrates career development tools such as job boards, internship listings, and portfolio building resources. Students can gain valuable information from industry experts, attend career fairs, and showcase their work to potential employers. MySCAD is a virtual starting point for students as they transition from academia to the professional world.
In a dynamic educational environment, technology has become a driving force transforming traditional teaching methods. MySCAD, an acronym for My School of Computer-Aided Design, is at the forefront of this educational revolution. This article examines various aspects of MySCAD, highlighting its features, benefits, challenges, and impact on both students and teachers.
Importance of MySCAD in Education
Educational technology is fundamental to providing effective learning. MySCAD plays a key role in this context by providing a platform that seamlessly integrates digital tools and traditional educational systems. Its importance lies in its ability to meet diverse learning needs and adapt to an ever-changing educational environment.
MySCAD Features and Functions
User-friendly interface
One of the distinctive features of MySCAD is its intuitive and user-friendly interface. The platform is easy to navigate, allowing students and teachers to focus on content rather than technology.
course management
MySCAD provides robust course management tools that enable educators to efficiently organize and create courses. The platform streamlines the entire process, from lesson planning to resource allocation, saving teachers valuable time.
collaboration tools
Encouraging collaboration is at the core of MySCAD’s design. Real-time collaboration tools allow students to participate in group projects, developing the teamwork and communication skills important in today’s professional world.
How MySCAD Increases Student Engagement
interactive learning materials
MySCAD goes beyond traditional textbooks to provide interactive learning materials that engage students and make complex concepts easier to understand. Engaging content increases retention and leads to deeper understanding of the subject.
Discussion forum
The platform has a dynamic discussion forum where students can actively participate in academic discussions. Not only does this promote critical thinking, but it also creates a sense of community among students and breaks down the walls of the physical classroom.
real-time feedback
Timely feedback is essential to student growth. MySCAD’s real-time feedback feature allows teachers to provide instant assessments so students can quickly address weaknesses and excel in their studies.
Benefits for teachers
Simplified assessment
Grading is a time-consuming task for educators. MySCAD automates and streamlines the grading process, allowing teachers to focus on providing constructive feedback and personalized student learning.
Customizable course content
Flexibility is key in education. MySCAD allows instructors to customize course content to meet students’ unique needs and learning styles. This adaptability improves the overall learning experience.
Case Study: Success Stories Using MySCAD
Real-life examples highlight the success stories of educational institutions that have implemented MySCAD. These case studies demonstrate the tangible benefits of integrating MySCAD into your learning environment, from improved student achievement to increased teacher satisfaction.
Future developments and updates
In the rapidly changing world of technology, MySCAD continues to evolve. This article describes upcoming developments and updates, and gives readers an idea of how the platform strives to remain at the forefront of educational technology.
Tips for using MySCAD effectively
To get the most out of MySCAD, teachers and students can follow the practical tips outlined in this section. From using advanced features to creating a comfortable online learning environment, these tips will ensure a seamless experience.
Problems and solutions
No technology is without problems. This section examines common problems faced by MySCAD users and offers practical solutions to overcome them and promote a positive and productive learning experience.
Integrate MySCAD into various learning environments
This article examines the integration of MySCAD into a variety of learning environments, from traditional classrooms to remote and hybrid environments, demonstrating MySCAD’s adaptability. Analysis of successful implementation strategies provides a road map for educational institutions.
Comparison with other educational platforms
Benchmarking differentiates MySCAD from other educational platforms and highlights its unique features and benefits. Readers will gain a thorough understanding of how MySCAD stands out in the crowded edtech landscape.
Conclusion:
MySCAD is a testament to Savannah College of Art and Design’s commitment to providing a comprehensive and enriching educational experience. MySCAD seamlessly integrates academic support, campus life, collaboration tools, and career development resources to help students unleash their creative potential and set them on a successful path in the dynamic and competitive field of art and design. We’ll help you get started. As technology continues to shape the educational landscape, MySCAD continues to be at the forefront of demonstrating how digital platforms can enhance the creative learning experience.
Tech
Features Of Integremos: A Complete Guide On Integremos Features And Usage

Welcome to the comprehensive guide on Integremos, a powerful platform designed to streamline your business processes and enhance productivity. In this guide, we’ll explore the key features and usage of Integremos, shedding light on how it can revolutionize the way you operate.
What is Integremos?
Integremos is a cutting-edge business integration solution that facilitates seamless communication and collaboration across various departments within an organization. It acts as a central hub, connecting disparate systems and applications to ensure a smooth flow of information.
Key Features of Integremos
Seamless Integration
Integremos excels in integrating with diverse software applications, eradicating data silos and promoting a unified workflow. Its adaptability ensures compatibility with your existing tools, making the transition seamless and hassle-free.

User-Friendly Interface
Navigating through Integremos is a breeze, thanks to its intuitive and user-friendly interface. Whether you’re a tech-savvy professional or a novice, you can harness the power of Integremos effortlessly.
Advanced Data Analytics
Unlock the potential of your data with Integremos’ robust analytics capabilities. Gain valuable insights into your business operations, enabling data-driven decision-making for sustainable growth.
Customization Options
Tailor Integremos to suit the unique needs of your business. Enjoy the flexibility of customization, ensuring that the platform aligns perfectly with your specific requirements.
Collaboration Capabilities
Foster collaboration among your team members with Integremos’ collaborative features. Break down communication barriers and encourage teamwork for increased productivity.
Security Measures
Rest easy knowing that your data is secure with Integremos. The platform employs advanced security measures to protect sensitive information, ensuring compliance with industry standards.
Customer Support
Experience top-notch customer support with Integremos. A dedicated team is ready to assist you, ensuring a smooth and satisfying user experience.
Benefits of Using Integremos
Increased Efficiency
By streamlining processes and reducing manual intervention, Integremos significantly enhances operational efficiency. Tasks that once took hours can now be completed in minutes.
Time and Cost Savings
Integremos is designed to save both time and money. Automate repetitive tasks, minimize errors, and allocate resources more effectively, leading to substantial cost savings.
Enhanced Decision-Making
Access real-time insights and analytics through Integremos, empowering you to make informed decisions that drive your business forward.
Real-Time Data Access
Integremos provides real-time access to critical data, ensuring that you are always up-to-date with the latest information. Stay ahead of the competition with timely and accurate insights.
Scalability
Grow your business without constraints. Integremos is scalable, adapting to your evolving needs and accommodating increased data volumes effortlessly.
Success Stories
Case Study 1: Company X
Company X implemented Integremos to streamline their inventory management. The result? A 30% reduction in operational costs and a 20% increase in overall efficiency.
Case Study 2: Organization Y
Organization Y integrated Integremos to enhance communication between remote teams. The outcome was a 40% improvement in collaboration and a 25% boost in project completion rates.
FAQs
What industries benefit from Integremos?
Integremos caters to a wide range of industries, including finance, healthcare, manufacturing, and more. Its versatility makes it a valuable asset for any business looking to optimize its processes.
How does Integremos ensure data security?
Integremos employs robust encryption methods and follows industry best practices to ensure the security of your data. Regular audits and updates further enhance its security measures.
Can I integrate Integremos with other software?
Yes, Integremos is designed for seamless integration with various third-party software applications. This interoperability ensures that you can connect Integremos with your preferred tools.
What kind of customer support does Integremos offer?
Integremos provides 24/7 customer support, ensuring that you receive assistance whenever you need it. The dedicated support team is knowledgeable and committed to resolving your queries promptly.
Is training provided for using Integremos?
Yes, Integremos offers comprehensive training programs to ensure that users can maximize the benefits of the platform. From basic functionalities to advanced features, training is tailored to your needs.
How can Integremos enhance collaboration among team members?
Integremos promotes collaboration through features such as real-time document sharing, task assignments, and centralized communication channels. These tools facilitate efficient teamwork and communication.

Conclusion
In conclusion, Integremos stands as a game-changer in the realm of business integration. With its robust features, seamless integration capabilities, and user-friendly interface, it is poised to elevate your business operations. Embrace the future of streamlined workflows and enhanced collaboration with Integremos.
-

 News2 years ago
News2 years agoVaping: Beyond the Hype – Unveiling the Risks and Realities
-

 Fashion2 years ago
Fashion2 years agoWhat is λιβαισ? A Complete Guide
-

 Entertainment2 years ago
Entertainment2 years agoUnleashing Geekdom: Exploring the Wonders of Geekzilla Radio
-

 Games2 years ago
Games2 years agoHow to Download Games From ApunKaGames: A Comprehensive Guide
-

 Fashion6 months ago
Fashion6 months agothesparkshop.in/bear-design-long-sleeve-baby-jumpsuit
-

 Life style1 year ago
Life style1 year agoDemystifying λυσασ: Unveiling the Enigmatic Concept
-

 News6 months ago
News6 months agoUnlocking the Magic of Gemstones: A Comprehensive Guide
-

 Fashion6 months ago
Fashion6 months agoThesparkshop.In Clothing Men
